, is a protocol accustomed to securely log onto remote techniques. It truly is the commonest technique to access distant Linux servers.
We will show While using the ssh-copy-id command below, but you can use any on the ways of copying keys we discuss in other sections:
This article explores the importance of SSH UDP Personalized tunneling, how it really works, and the advantages it provides for network protection in.
In relation to our air-con models, we regularly listen to about the necessity of Freon. But how…
You may be prompted to set a password on The real key files them selves, but this is a reasonably unusual follow, and you must press enter from the prompts to accept the defaults. Your keys will be created at ~/.ssh/id_rsa.pub
Warning: Before you decide to proceed with this particular action, be certain you have got installed a public key on your server. Normally, you'll be locked out!
But with numerous VPN services to pick from, and all of these boasting to be the most effective, you should know you will discover merely a handful which might be well worth
port is specified. This port, within the remote host, will then be tunneled to a host and port mixture that's connected to with the local Laptop. This allows the remote Computer system to access a ssh udp host as a result of your local computer.
It is often a good idea to totally disable root login as a result of SSH Once you have create an SSH person account that has sudo privileges.
An SSH vital commences its life on your neighborhood equipment. It is made of two elements: A non-public essential, which you in no way share with any person or everything, and also a public one particular, SSH UDP which you copy onto any remote equipment you wish to have passwordless entry to.
Also Observe that Home windows installers are actually built with NSIS Model which has been patched versus free ssh 30 days numerous NSIS installer code execution and privilege escalation issues.
SSH usually operates on port 22, and that is the normal port for setting up SSH connections. Nevertheless, SSH could be configured to utilize a distinct port if required.
If you don't have password-dependent SSH accessibility out there, you'll need to insert your general public vital towards the distant server manually.
Targeted visitors that is certainly handed to this community port is going to be despatched on the distant host. From there, the SOCKS protocol will probably be interpreted to determine a connection to the specified finish place.
 Dylan and Cole Sprouse Then & Now!
Dylan and Cole Sprouse Then & Now! Romeo Miller Then & Now!
Romeo Miller Then & Now!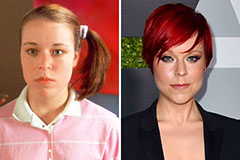 Tina Majorino Then & Now!
Tina Majorino Then & Now!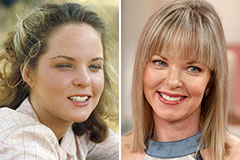 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Dolly Parton Then & Now!
Dolly Parton Then & Now!